This is a common question that many people ask and the thoughts behind this subject have changed over the years and even recently they have changed slightly. If you work in IT or wanna work in IT you will be most likely asked this question once or twice (a week).
Passwords have been around for a long time and for a long time have been our primary way of securing accounts. For a long time, there never were really restrictions so people could make passwords whatever they want. We did quickly learned that this was a horrible idea because everyone used passwords that were easy to remember and in turn were easy to guess.
Improving Our Passwords
We did improve and realized that we needed to improve how we choose our password. Most companies implemented specific rules to help people choose more secure passwords.
At least 8 characters. This rule was created for a couple of reasons. The first is because of the longer the passwords the better. The other reason was earlier versions of the Microsoft Operating systems stored password in parts of 7 characters before it was encrypted. So an 8 character or longer password would have two separate encryption being done on the password.
Include special characters and numbers. This rule was created for obvious reasons. When you include additional characters you increase the number of possibilities you have to guess a password. So let us do some quick math. I have a 10 character password that is only letters which would give me 141,167,095,653,376 possibilities (26 letters in the alphabet and 10 possibilities 26^10). This may seem like a lot of possibilities but it takes no time for a computer to run through this list. Also, this is only lower case letters since all passwords are case sensitive you can then see. If you add in upper and lower case letters you get 144,555,105,949,057,024 (52^10). But again a computer an run through this pretty fast. So now if we add numbers and special characters you can imagine the possibilities. This would give you 72^10 or 3,743,906,242,624,487,424. So you can quickly see how increasing the number of possible characters increases the possibilities
Adding in these rules for creating your password certainly, create many more possibilities for someone to have to go through. But unfortunately, these rules have brought us to the point where passwords are not only created with predictable patterns but are reused over and over again.
Password Reuse it Bad
If you have a single password that you use for everything then you should probably re-think some choices you have made. I know that having a single strong password is nice and makes things a lot easier but if a single service that you use becomes compromised that single password you use could be used against you in other services.
Using the service HaveIBeenPwned.com you could see that my personal email address was discovered in two separate data breaches. The first was a LinkedIn data breach back in 2016 and the second was a data breach in MyFitnessPal in 2018. If my password for both either of those services was the same password I used for say Gmail then it is possible that anyone who obtained the list of usernames and passwords from those breaches would be able to access my Gmail account. When a malicious person takes a list of accounts that been obtained from a data breach and they try them on other sites this is called credential stuffing. They are counting on people reusing the same username and password for multiple accounts. I have seen first hand this being done to large websites.
So bottom line is do not reuse password.
So what should we do?
Troy Hunt who is an icon in the security community and very widely know I think says it the best.
The best password is the one you don’t remember.
Troy Hunt
Now I am sure you are thinking well that is nonsense how can you use a password that you don’t remember. This is where password managers come into play. There are plenty of them out there and my personal favorite is LastPass and 1Password. [Full Disclosure: I am an affiliate of LastPass and if you use my affiliate link I get a small commission]
Password managers keep track of all of your passwords for you so you don’t have to. They will also generate a random password when you need it and these types of services are available across multiple devices and browsers.
Every service I use has between a 16 a 32 character password (depending on what the service will support) that I do not know. When I access the service or site I use my password manager to fill in the password field. This saves me quite a bit of time as well as making all of my accounts more secure. As a special note, LastPass will even warn you if you use the same password across multiple sites.
These services are paid but LastPass does have a free option that gives you a lot of functionality. These sites also do require a “Master Password” in order to access them so how do we create a secure “Master Password” that we will remember
Passphrases
Passphrases a way of creating a secure password. Instead of using a random string of characters that is difficult to remember you use a sentence that is easy with some simple substitutions.
So for example, if I like kayaking I could use the sentence “I love kayaking during the summer”. Then I could make that a passphrase with something like “1 L0ve Kayaking During The Summ3r”. Now let’s take our formula from earlier and see how many possible combinations.
72 (upper case, lower case, numbers, special characters) and then 33 characters in my passphrase. That would be 72^33 which comes to
19587201101044934534632290247568981600656724171840497964285952
Pretty crazy right?! I am sure that is much easier to remember than $Rt3#43fdkjt%^! right?
Multi-Factor Authentication
Something else that is offered by these password managers is Multi-Factor Authentication and I am a huge proponent for MFA.
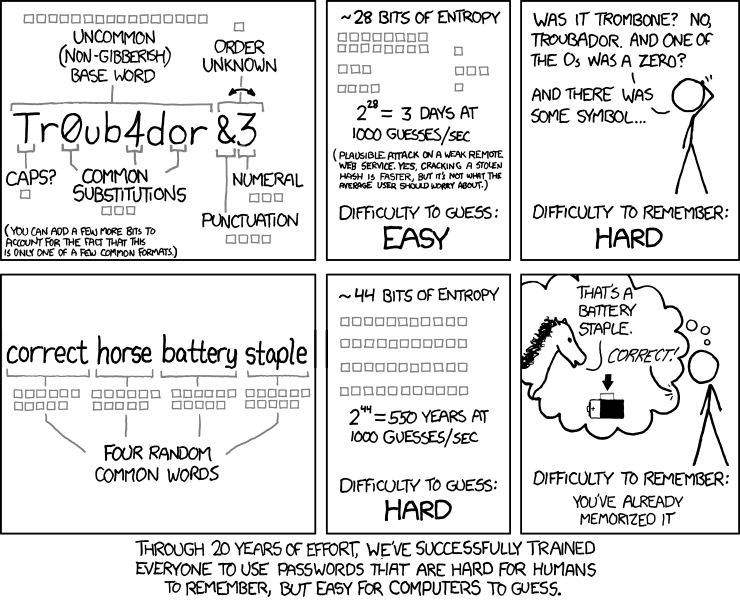
This post is getting quite long so I will same the details of Multi-Factor Authentication for another post to come soon. But I will leave you with a great KXCD comic that pretty much sums up much of this post.